Setting up an Azure Active Directory application to retrieve Let’s Encrypt certificates
So you might remember me posting about using the Let’s Encrypt site extension for Azure App Services, called Azure Let’s Encrypt, created by SJKP.
This has quite well for over a year now and even works for Function Apps.
However, last month I got notified my SSL certificate was expired on one of my sites. Strange, as an automated job should just handle this for me. I thought the job probably didn’t execute because of some glitch in the matrix. Therefore I logged in manually, started the site extension wizard again and was stuck on this screen.
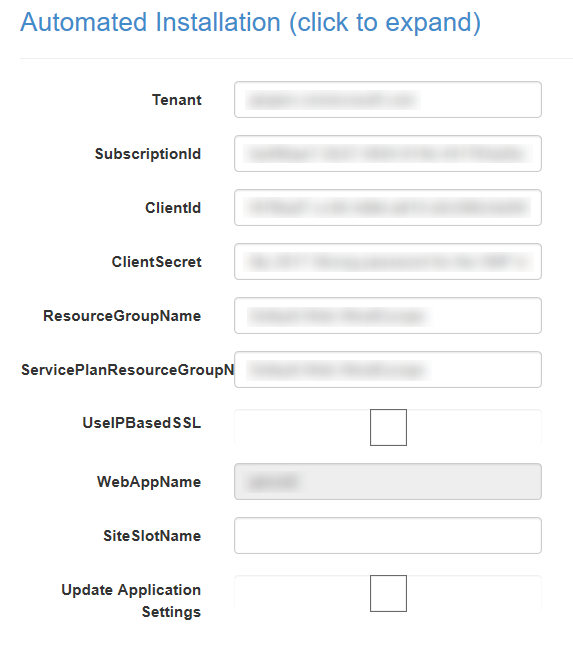
The reason I was stuck was because the ClientId and ClientSecret didn’t work anymore. As these settings hadn’t changed since I started using this extension I found it quite strange.
Apparently, the Server Principal, which I had created last year, somehow had changed and I didn’t know how to change it back. Lucky for me, managing the AAD isn’t very hard to do nowadays. With a bit of trial and error I was able to create a new SNP and use these details on the Let’s Encrypt site extension.
Creating a new application in AAD
First thing you need to do is add a new Appliction to your AAD. Be sure to pick the option App registrations over here and press the New application registration.
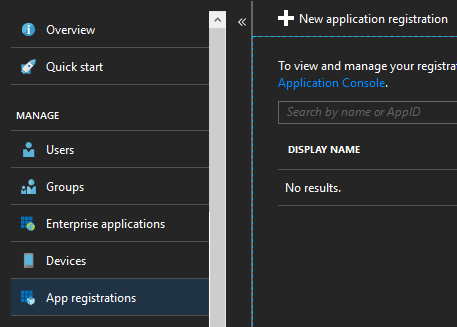
When creating an application you have to specify a name, I chose LetsEncrypt and which type it is. Just choose the Web app/ API option over here. The other mandatory field called Sign-on URL isn’t used in our scenario so you can use any URL you like.
When your application is created you’ll see be navigated to the overview page of this application. Be sure to copy the Application ID from over here as you need it later on. This value has to be used as the ClientId in the site extension.
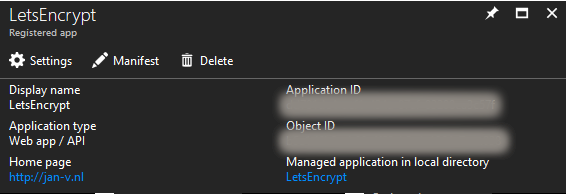
Next thing we need to do is add a Key to this application. You can add new keys by Settings link and choose the Keys option. This key will be used as the Client Secret. Be sure to copy the value after saving as this is the only time you’ll be able to see it.
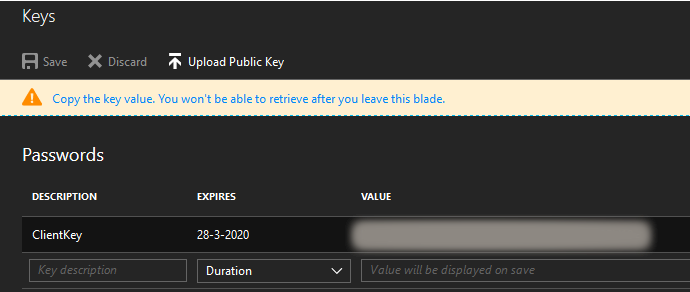
Also note the Expires option.
The default expiration date is set to 1 year from now. This has led me to believe the ClientSecret of my earlier SNP is probably expired. In hindsight I could probably have updated the value in my old SNP and be done with it.
We now have everything we need from our application, so the next thing is to set up the resource group.
Set up your resource group
We need the newly created application to do stuff inside our resource group. Therefore we need to add some permission to it.
To do so, head down to the resource group which contains your app service(s) and pick the Access control (IAM) option.
![clip_image001[5]](https://jan-v.nl/files/33f28d8f-aa89-447f-a9ae-e7f016ad28c9.png)
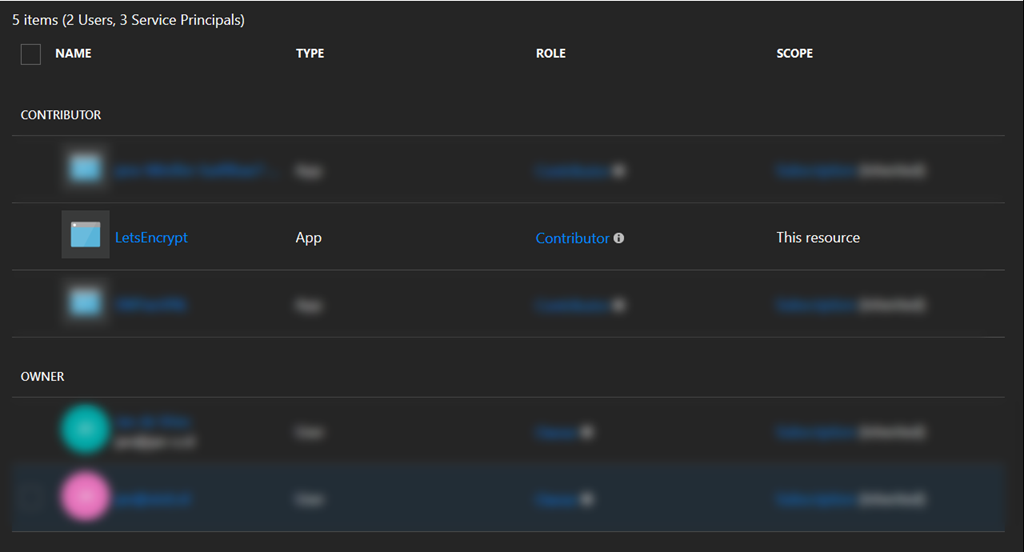
From over here you can select your newly created application and grant it the Contributor role.![clip_image001[7]](https://jan-v.nl/files/c477cd2d-bb6f-4af2-a722-d9b64bfd3642.png)
If everything goes well you’ll see the application is added to the list of contributors of this resource.
Running the wizard again
Everything should be set up correctly now so you can head back to the wizard of the site extension. Be sure to fill out the ClientId and ClientSecret with the newly retrieved values from the application.
After doing so and trying to proceed to the next screen I was prompted with the message _The ClientId registered under application settings [guid] does not match the ClientId you entered here [guid]_ as you can see in the screenshot below.

The first time I ran this wizard (a year ago) it was able to create and update the application settings of the App Service. Apparently this has changed and I had to change the Application Settings by myself in the App Service before I was able to continue in the Let’s Encrypt site extension.
For completeness sake, if you’re running a Function App, you can find the settings under All settings, which will navigate you to the App Service settings.
![clip_image001[9]](https://jan-v.nl/files/838c7f31-ad9a-48b6-a7d6-72406a7f6960.png)
After you’ve changed these settings you should be able to proceed and continue with requesting your SSL certificates.
That’s all there is to it!
Hope it helps whenever you run into problems if your SNP doesn’t work anymore. As I already mentioned, in hindsight it would probably have been much easier by just updating the Key of my original SNP, which I’ll probably need to do in 2 years from now when this new secret will expire.
