Setting up a VPN connection to an Azure Virtual Network
One of the reasons for me to create an Azure virtual network is being able to connect to my development machines in the Cloud from anywhere, without exposing them to the public. In order to do so, all machines have to be added to the virtual network. You also have to select the option to set up a point-to-site VPN connection to the virtual network.
Setting up a point-to-site VPN connection to an Azure virtual network is documented quite well on the Azure documentation pages. Still, I have come across a couple of problems which I’d like to share.
The first problem I had was executing the makecert program via the Visual Studio Command Prompt on my machine. This tool is really useful when creating a self-signed certificate.
d:\Temp\vpnblog>makecert -sky exchange -r -n "CN=RootJanHome" -pe -a sha1 -len 2048 -ss My "RootJanHome.cer"
'makecert' is not recognized as an internal or external command, operable program or batch file.
Apparently the makecert program isn’t installed by default on your machine when installing Visual Studio 2015. You’ll have to install the Windows 10 SDK and tools in order to get it. To fix it, just Modify your Visual Studio installation and select the option which installs these bits.
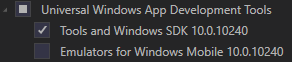
It takes some time, but when the installer is finished, you can start creating your certificates. First you’ll need a root certificate which will has to be uploaded to your virtual network.
# Root certificate
d:\Temp\vpn>makecert -sky exchange -r -n "CN=RootJanHome" -pe -a sha1 -len 2048 -ss My "RootJanHome.cer"
Succeeded
# Client certificate
d:\Temp\vpn>makecert -n "CN=ClientJanHomeUbook" -pe -sky exchange -m 96 -ss My -in "RootJanHome" -is my -a sha1
Succeeded
The second statement creates a client certificate, using the former created root certificate, which will be used for authentication when setting up the VPN.
These certificates will get stored in the Current User/Personal store.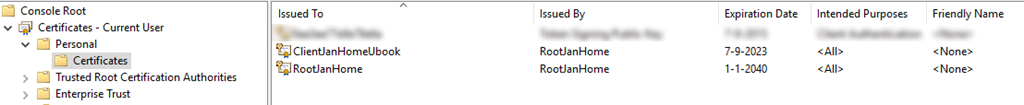
I’ve created several other client certificates for my other machines as well which have to be exported in order to install them on the corresponding clients.
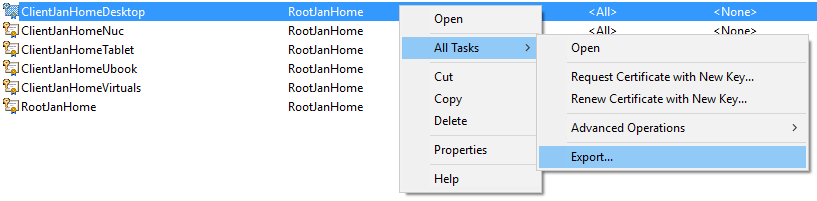
Make sure you are also exporting the private key of the certificates, otherwise they will be quite useless for authentication.
After having created all necessary certificates it’s time to upload the self-signed root certificate to your Azure virtual network.
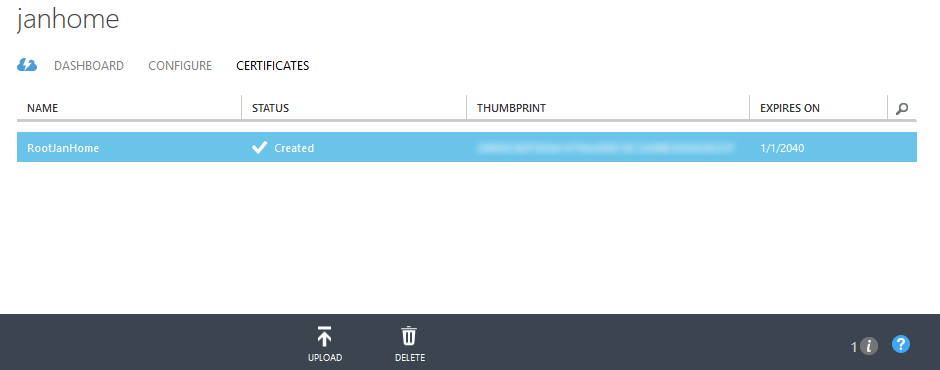
The management portal provides a nice button to upload these type of certificates.
Having finished this initial setup you are ready to download the VPN client from the virtual network dashboard. Select the correct one matching your bits of the OS.
This application, which isn’t signed, creates a VPN connection for you which, in theory, you should be able to use.
Pressing the Connect button for this VPN connection will prompt you with a pop-up having another Connect button.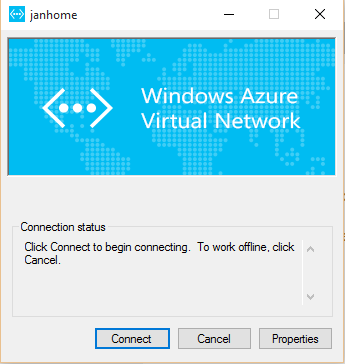
When pressing the Connect button a warning will be shown telling you the assembly cmroute.dll wants to update the routing table. As this software came from Microsoft I’d say it’s fairly safe to let the assembly modify your routes.
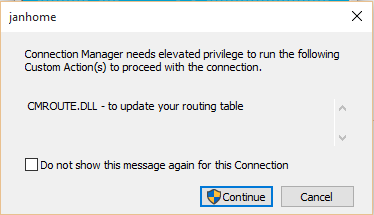
Pressing the Continue button will show the next problem I encountered. The connection can’t be established:
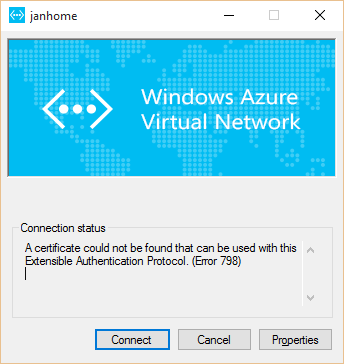
A certificate could not be found that can be used with this Extensible Authentication Protocol. (Error 798)
When this happens, it’s possible there are some errors with your certificates. In my case I am sure the certificates are correct, so something else is up.
I’m not sure why this error occurs, but do have a solution: Create the VPN connection by yourself!
The tool already created a VPN connection which has the gateway address in it.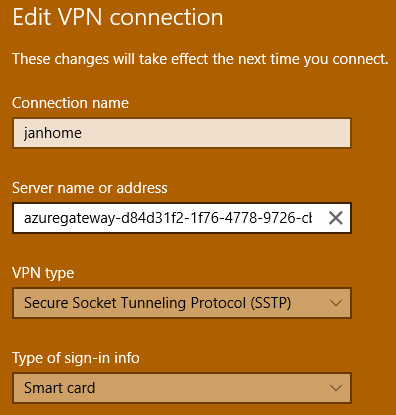
Copy these settings to a new VPN connection, for example janhome_manual.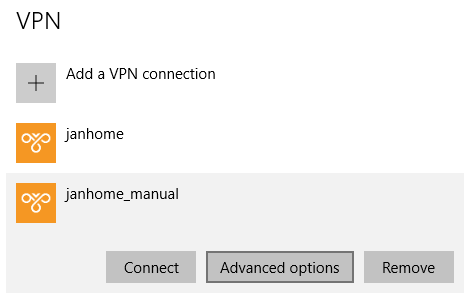
Make sure the Security settings of this VPN connections uses a Smart Card for authentication.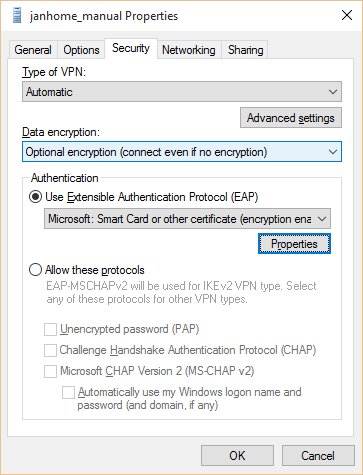
You can also specify in the IPv4 properties not using the gateway of the virtual network. This is especially useful if you still want to use the internet when connected to the VPN.
If you have set this up correctly a connection can be made to the virtual network using your client certificate.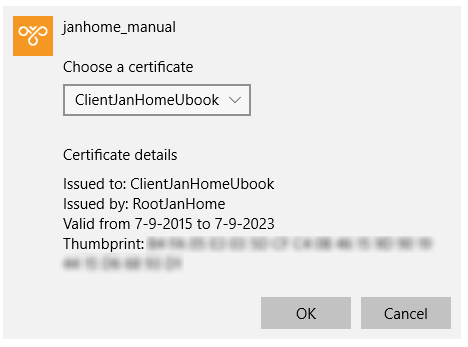
The first time I was connecting to the virtual network I received the following error message:
The remote access connection completed, but authentication failed because the certificate that authenticates the client to the server is not valid.
Ensure that the certificate used for authentication is valid.
The reason for this error was on my behalf. While troubleshooting the problems I had, I had created and uploaded a new root certificate, but hadn’t uploaded this to the virtual network yet.
I do hope you are able to set up a VPN connection with a bit more ease as I had.
