Getting the group claims when authenticating with Azure Active Directory
I started working on some internal web applications for a customer. For these types of applications, it makes a lot of sense to use Azure Active Directory to authenticate users and use their AAD groups/roles to authorize them on specific pages.
I wanted to authorize users by the AAD groups they are placed in. Some users can access Production data, while others are only allowed to access data from the Test environment, all based on the groups they are in. Because this is already configured by our system administrators, I want to use these groups for my application(s) also.
This sounds easy enough, and it is, but you have to do some manual work in Azure Active Directory to make this possible. It took me too much time for my liking, so I hope this post helps others (and myself) in the future.
One of the first things you need to do is create a new App Registration in the AAD and give it permission to User.Read.All to read the users’ claims.
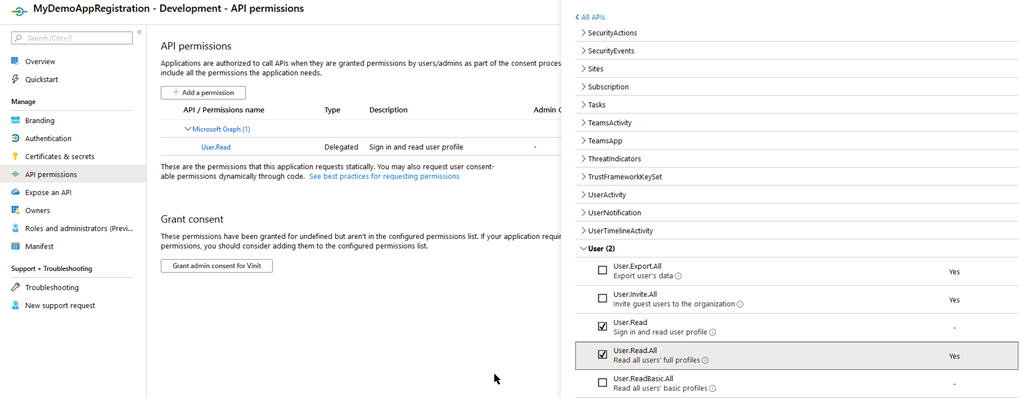
This requires consent from your Administrator, so make sure they are available or you have enough permissions yourself to do this.
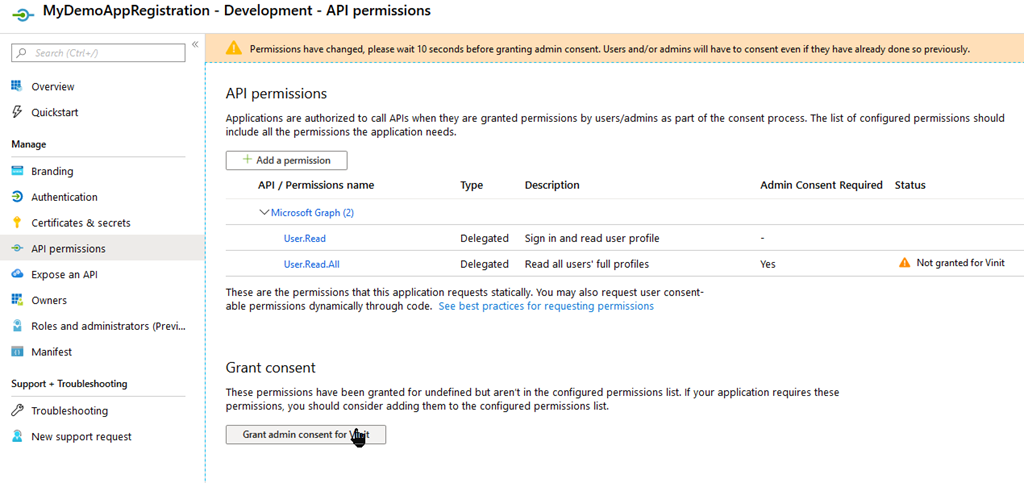
When this is set up correctly, head to the Manifest blade.
You’ll see a lot of JSON over here, but the property you are looking for is called groupMembershipClaims. This property is probably set to null, but this needs to be changed to All to get all of the AAD groups/roles for a user.
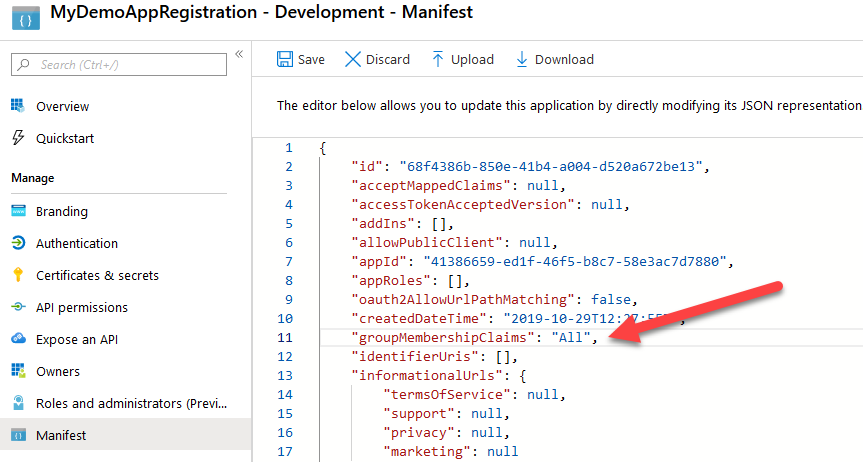
You should be able to see the AAD groups inside the token of your users. This will help a lot if you need to authorize users for specific pages or API calls.
