Use Tailscale Github Action to connect to your home network
I have been a long time user of Tailscale, a very easy to use VPN mesh system, to connect to my home network when I’m not at home. There are other solutions, like NordVPN Meshnet, but I learned about Tailscale first. It’s especially useful when using your local DNS (PiHole) and taking advantage of the sites blocked by it.
Currently, I’m in the process of self-hosting services a bit more. Relying in (free) cloud services that might be turned on/off at a moment notice or removing features I use is something I’ve seen happen a bit too much lately.
Because of this, I’m running a container of Linkwarden to act as a ‘Read it later’ or bookmarking service. I was using Omnivore for this, but that service got shut down at some point.
Some of the links I store in Linkwarden might also be interesting for others who might have missed them. I wanted to get a list of these links and share them on my site, which is why there’s now a Weekly Links Archive. These pages contain all links I find interesting enough to share over here.
Because I’m a firm believer in automation, these pages are created via a GitHub Action workflow.
Connect GitHub Action to Tailscale
It turns out, Tailscale is providing a GitHub Action that can be used to connect to your tailnet.
By adding the below step to your workflow, all subsequent steps are able to connect to your tailnet.
- name: Tailscale
uses: tailscale/github-action@v3
with:
oauth-client-id: ${{ secrets.TS_OAUTH_CLIENT_ID }}
oauth-secret: ${{ secrets.TS_OAUTH_SECRET }}
tags: tag:link-collector
use-cache: true
Create an OAuth client for your GitHub Action
In step shared earlier you can see two secrets are being used, TS_OAUTH_CLIENT_ID & TS_OAUTH_SECRET. These are used to authenticate the action.
A new OAuth client can be created in the Settings of your admin console on the page called ‘OAuth clients’
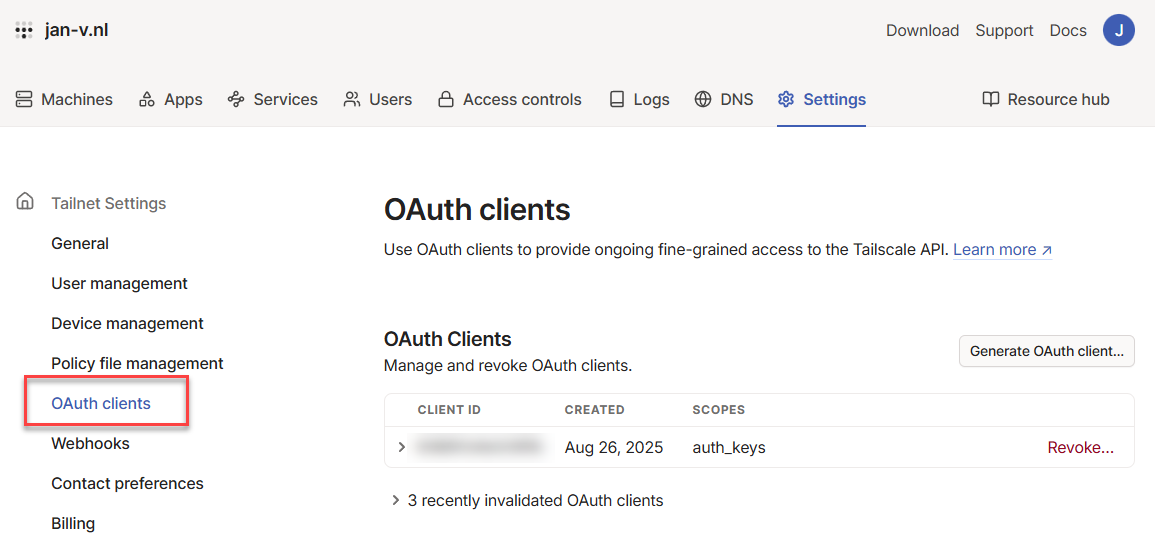
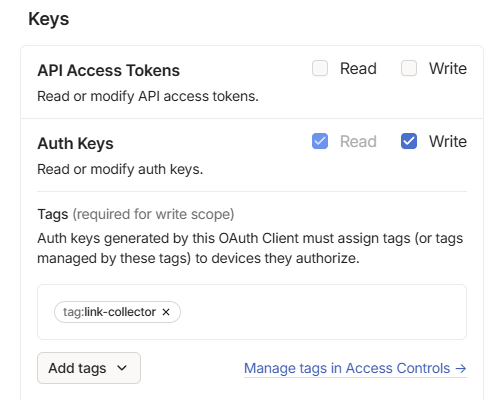
Over yere you can press the ‘Generate OAuth client…’ and check the Write scope under Auth keys. NOT the OAuth Keys (ask me how I know)!
When you select this, you must also specify which tags are allowed to use this client. As shown in the GitHub Action, I’ve used the tag link-collector, so this also has to be selected over here.
Create a tag
Tags are created on the page ‘Access controls -> Tags’.
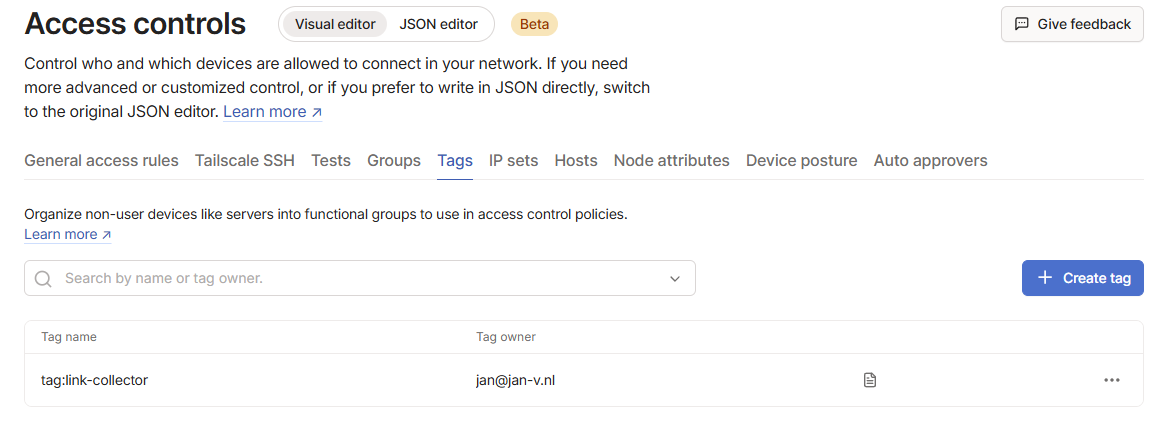
You can create multiple tags setting permissions quite granular.
This has to be done before creating an OAuth client for this purpose.
You’re done!
That’s all there is to it!
If all is set up correctly, you will see a message stating Attempt 1 to bring up Tailscale... in your logs.
All subsequent steps in your workflow will now be able to communicate to your tailnet. I’m using it to connect to my NAS, which is hosting Linkwarden in a container, so sending API requests towards http://192.168.2.31/ and it’s working like a charm.
However, if the setup of the OAuth client isn’t done correctly, you might see some 403 messages in the logs.
Attempt 1 to bring up Tailscale...
Status: 403, Message: "calling actor does not have enough permissions to perform this function"
Tailscale up failed. Retrying in 5 seconds...
Attempt 2 to bring up Tailscale...
Status: 403, Message: "calling actor does not have enough permissions to perform this function"
Tailscale up failed. Retrying in 10 seconds...
Attempt 3 to bring up Tailscale...
Status: 403, Message: "calling actor does not have enough permissions to perform this function"
Tailscale up failed. Retrying in 15 seconds...
Attempt 4 to bring up Tailscale...
Status: 403, Message: "calling actor does not have enough permissions to perform this function"
Tailscale up failed. Retrying in 20 seconds...
Attempt 5 to bring up Tailscale...
Status: 403, Message: "calling actor does not have enough permissions to perform this function"
Tailscale up failed. Retrying in 25 seconds...
In my case this was due to having selected the wrong scope and tag for my OAuth client. In hindsight, it’s an easy fix but took me a bit of time to figure out.
